Ryan Ethical Hacker: Cybersecurity Insights & Expert Analysis
In an era defined by relentless technological advancement, is our digital world truly secure? The answer, unfortunately, is a resounding no, and that's where ethical hackers, like Ryan, become the unsung guardians of our interconnected lives.
Ryan, a name synonymous with expertise and trust in the realm of ethical hacking, stands as a testament to the critical role cybersecurity professionals play in the modern age. He is not just a practitioner; he's a pioneer. By leveraging his profound understanding and skills, Ryan empowers organizations to identify and fortify their digital defenses, ensuring the protection of sensitive information in an increasingly hostile online environment.
This exploration delves into the captivating world of Ryan, an ethical hacker, tracing his journey, celebrating his achievements, and examining his contributions to the cybersecurity community. Whether you're a newcomer to the field or a seasoned veteran, the following insights offer a valuable perspective on the ever-evolving landscape of ethical hacking.
- Laurie Buffett Biography Impact In Finance
- Maite Perroni William Levy A Look At Their Lives Love Story
| Biography |
|---|
|
From his early fascination with computers and technology, fueled by an innate curiosity, Ryan embarked on his cybersecurity journey. His relentless dedication and commitment propelled him to become a respected authority in the field of ethical hacking.
Ethical hacking, at its core, is the practice of authorized intrusion into systems and networks to unearth vulnerabilities that malicious actors could exploit. Ryan, an expert in this domain, helps organizations prepare themselves to proactively face cyber threats. Key aspects of this practice include penetration testing, vulnerability assessment, security auditing, and risk management.
A report by Cybersecurity Ventures projects that global spending on cybersecurity will surpass $270 billion by 2026, a figure that unequivocally underscores the ever-growing importance of ethical hacking in protecting digital assets.
Ryan's path into the world of ethical hacking began during his college years. His innate ability to identify system vulnerabilities set him apart. After earning his degree in Computer Science, Ryan dedicated himself to mastering the art of ethical hacking.
His career is marked by a series of significant milestones, including certifications like Certified Ethical Hacker (CEH) and Offensive Security Certified Professional (OSCP). These credentials serve as clear evidence of his extensive knowledge and experience, further solidifying his reputation as a trusted and sought-after expert in the field.
Essential Tools for Ethical Hacking
Ryan's effectiveness is a direct result of his skillful use of a wide array of tools. The following are some of the most frequently used and vital:
- Nmap: This is a tool for network exploration and security auditing.
- Metasploit: A robust penetration testing framework used to discover vulnerabilities.
- Wireshark: A leading network protocol analyzer used for capturing and meticulously analyzing data packets.
- John the Ripper: A powerful password-cracking tool used to assess password strength.
These tools allow Ryan to conduct comprehensive security assessments and provide insightful, actionable recommendations to his clients.
Ryan has received numerous accolades that recognize his valuable contributions to the field of cybersecurity. Some of his notable achievements include:
- Identifying a critical vulnerability in a Fortune 500 company's system, resulting in the avoidance of millions of dollars in potential losses.
- Receiving the prestigious "Cybersecurity Professional of the Year" award at the International Cybersecurity Conference.
- Authoring a bestselling book that offers practical ethical hacking techniques.
Ryan's work has been consistently lauded by industry leaders and leading publications, further cementing his authority and influence within the field.
Addressing Modern Threats
Ryan confronts the most pressing cybersecurity challenges head-on. These include:
- Ransomware attacks, which have become increasingly sophisticated and prevalent.
- Phishing scams that exploit human vulnerabilities through deceptive tactics.
- Data breaches that compromise sensitive information and erode trust.
- IoT security vulnerabilities, as the Internet of Things expands, providing new attack vectors.
By consistently staying ahead of emerging threats and adapting to the evolving landscape, Ryan helps organizations remain resilient against cyberattacks.
For those aspiring to pursue a career in ethical hacking, Ryan offers this advice:
- Obtain a robust foundation in computer science and networking principles.
- Obtain relevant certifications to enhance credibility and demonstrate expertise.
- Maintain a current knowledge of the latest trends and emerging technologies in the cybersecurity world.
- Practice ethical hacking skills in carefully controlled and safe environments to build practical experience.
Ryan consistently emphasizes the importance of continuous learning and the critical need for ethical conduct in the dynamic field of cybersecurity.
Step-by-Step Approach
Ryan's structured process is carefully designed to ensure effective results. The approach includes:
- Reconnaissance: Gathering preliminary information about the target system.
- Scanning: Identifying active hosts, services, and open ports.
- Exploitation: Attempting to leverage identified vulnerabilities.
- Post-Exploitation: Analyzing the impact of a successful attack.
- Reporting: Documenting findings, providing actionable recommendations for remediation, and outlining steps taken.
This systematic approach is designed to help identify and address all potential vulnerabilities.
Ryan's influence extends far beyond his individual achievements. He has played a significant role in shaping the future of cybersecurity through his significant contributions to the industry. By generously sharing his knowledge and expertise, Ryan has inspired countless professionals to join the vital fight against cybercrime.
His involvement in cybersecurity conferences and workshops has also helped raise awareness about the importance of ethical hacking in today's digital age.
As technology continues to advance at an unprecedented rate, Ryan foresees several key trends in the cybersecurity landscape:
- Increased adoption of artificial intelligence for the detection of threats and the automation of security tasks.
- Greater emphasis on the adoption of robust cloud security solutions to protect data and infrastructure.
- The expansion of cybersecurity regulations and the constant evolution of compliance standards.
- More collaboration between governments and private organizations to proactively combat evolving cyber threats and enhance overall security posture.
Ryan's insights provide valuable guidance to both individuals and organizations as they navigate the ever-changing, dynamic world of cybersecurity.
Ryan, an ethical hacker, has established himself as a respected figure in the cybersecurity community and a symbol of expertise and trust. His work has made a substantial contribution to safeguarding our digital world. Understanding the principles and practices of ethical hacking enables individuals and organizations to better protect themselves and their valuable assets from the increasing threats of cybercrime.
We encourage readers to explore the resources and consider a career in ethical hacking. Your feedback and engagement are valuable to us, please leave a comment, share this article, or explore other content on our website for more insights into the world of cybersecurity.
- Tiger Woods His Relationships Inside His Love Life Career Impact
- Hailey Biebers Engagement Ring Style Worth More

Certified Ethical Hacker

A Day in the Life of an Ethical Hacker Internxt Blog
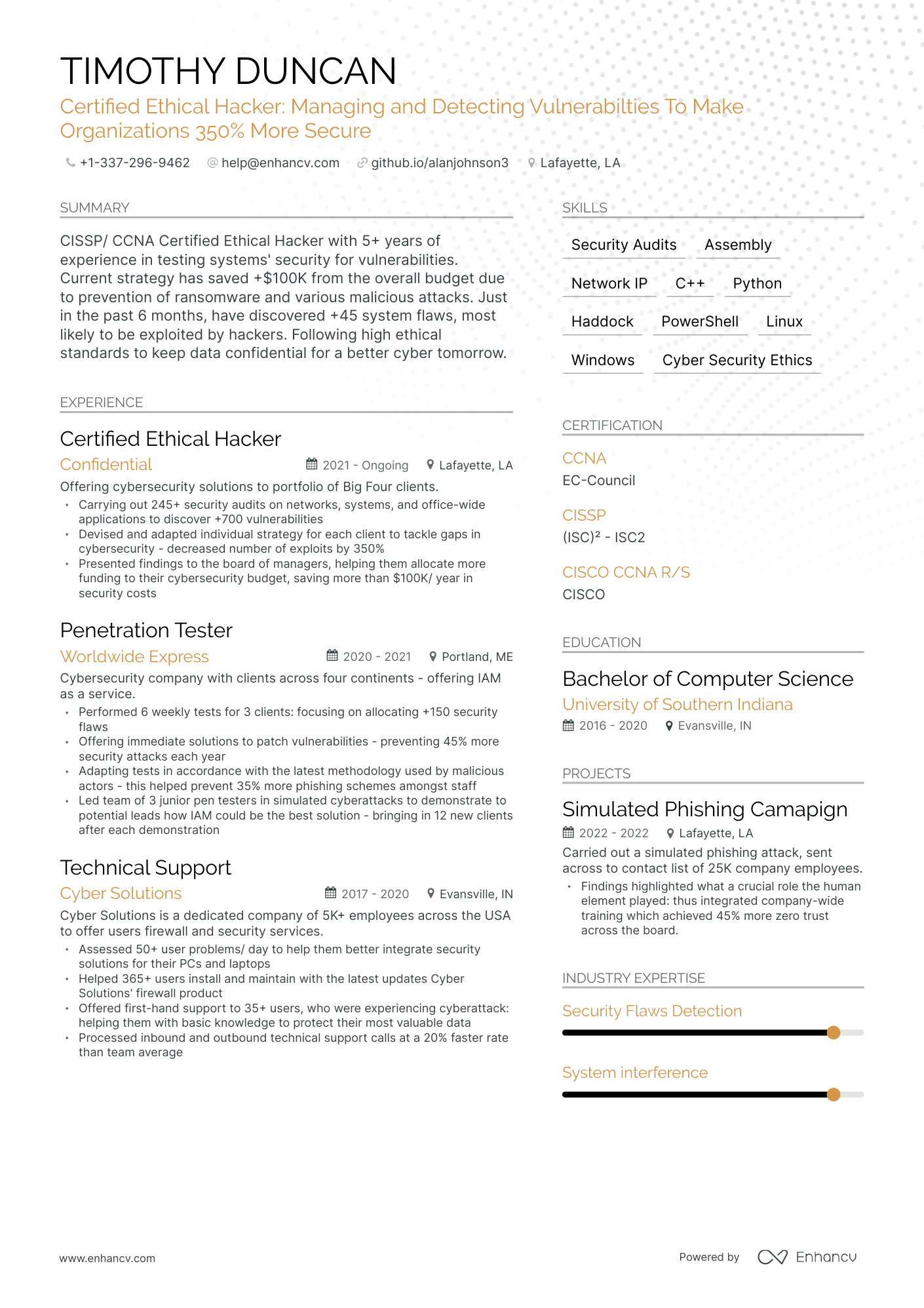
5 Ethical Hacker Resume Examples & Guide for 2023